DATA ANALYTICS
Our Smart Factory Transformations team uses data analytics every day to recommend and implement optimized factory solutions. We use the data to understand the flow, bottlenecks and capacity of the current state of your operations. Once we have the current state, the future state is developed in which we provide a roadmap to further improve your manufacturing process.
Streaming machine-level information can be analyzed and assessed in real-time to determine what parameters are important to produce a high quality item and quickly alert an operation if there is any variance. In high rate manufacturing, a machine malfunction can cause millions of dollars of waste if not caught in time.

The supply chain is getting more complex and harder to keep track of which suppliers produce high quality products as well as which suppliers deliver products on-time. The best data analytic solutions create visibility throughout the whole supply chain, allowing your team to make data driven decisions.
In the past, demand forecasting relied on analysis of historical data, typically found in multiple databases or spreadsheets. A data analytics solution offers a comprehensive view of data throughout your business. It can apply advanced analytics to identify recurring trends, issues and anomalies and then align it with customer sentiment data to gain a better understanding of future demand.
data analytics can help innovate in how your business operates, how to work with suppliers and customers and how to identify new revenue streams. Some companies have been able to use data analytics to create new business lines, creating new unexpected revenue streams. Our Smart Factory Transformations team can help your organization reach it’s full potential and grow.
CYBER SECURITY
Virtual Information Security Officer (vISO)
Your information security program must include safeguards designed to protect against both technical and human vulnerabilities. Because a security program incorporates more than just the network, best-practice guidelines suggest testing should go well beyond conventional network vulnerability scanning. Our Security Assessment is designed specifically to meet regulatory requirements and address the needs of any size organization. To determine the adequacy of your existing security controls and to identify security deficiencies, our assessment provides a thorough examination of your networks. Can you afford to hire a team of full-time cyber security experts? We have you covered with our vISO services 24/7.
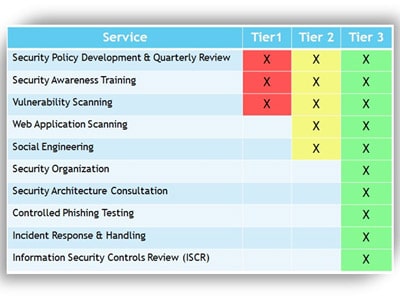
The Value of a Compliance Checkup
Information security is a need, not a luxury. Being a headline in the morning news is a major concern of all corporate executives. Taking proactive steps to improve your overall security today can help keep your company out of tomorrow’s headlines.
Designed using a modular approach, CREAN’s services can be dovetailed into any existing security architecture to give ongoing security protection and incremental improvement. The extensive experience of the CREAN team can be leveraged as needed, working with your IT provider to ensure complete compliance.
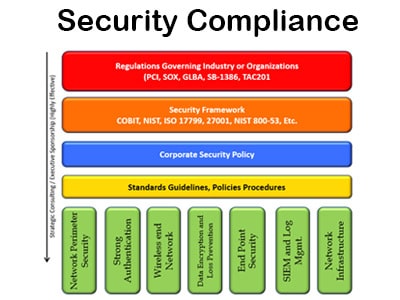
Quickly Assess Your Security Risk
Would you risk driving without car insurance or owning a home without home owner’s insurance?
Security threats are clearly increasing. If a breach happens, you must disclose it. With credit reporting and monitoring in today’s world, it is often the credit card companies who will tell you there has been a breach. Because the security landscape is changing, many original beliefs about small businesses are no longer true. All business, regardless of size is at risk.
“Who would attack us? We are too small for hackers.”
Based on a 2012 report from Verizon and the Secret Service breaches have increased from 4 million in 2009 to 361 Million in 2011. The #1 target was small businesses from 11 to 100 employees.
”We protect our data. We trust every employee.”
Does your company have users who can store information on a laptop or mobile device, or connect from their home machine? If so, do you trust their children’s friends? Additionally, the amount of data found in most companies’ trash cans is overwhelming. Without a full assessment you can only assume your company is secure.
“We have insurance in case of an attack or loss”
Insurance companies often times ask for a Security Assessment Questionnaire to be filled out. These documents are generally passed between Accounting and IT and are misunderstood or are filled out based on future plans. What were your answers?
Most require you have at least the following:
- Security Policies
- Vulnerability Scans performed
- Firewall and A/V
- Incident Response Plans
- Risk Assessment Performed
Often companies state they have all of these things in place when in fact they have none. If you don’t have the above list in place you may be left holding a very expensive bill. Our experts can quickly assess what your organizations’ security risk is and the steps to reduce those risks.
Start Your Path to Acceleration Today
Reach out to us and we'll work with you to find the right solution for your engineering or manufacturing needs.
